if you haven’t heard of cryptography before, you’re at the right place. The puzzles to solve in escape rooms are diverse and complex. In our missions, you will be dealing with clues and puzzles, and these may be encrypted.
So, you will need a lot of ingenuity and above all a good spirit of observation.
But moving on to the topic of this article, the first thing I have to ask you is do you know the history of cryptography? Its origins, when it was born and how it developed?
We today have tried to give you a summary of the most important milestones in the history of cryptography, from its inception to the present day.
So you can understand a little bit more about the puzzles to solve in an escape room, plus of course the fact that it is a very interesting topic and above all very broad. You should know that they even made a course of study!

The oldest images that come to mind when we talk about codes and cryptography are, surely, the Egyptian hieroglyphs carved in monuments or on papyri. In short, these secret communications are to be considered mysterious writings and date back more than 4,500 years.
Moving into the Middle Ages, cryptography, as well as the double-cross of a secret agent, immediately refer us back to Babington’s plot to eliminate Mary Stuart, Queen of Scots and pretender to the throne of England, held by Queen Elizabeth I. Perhaps some of you have seen some movies or TV series on this subject!

Another cryptography plot was the one that led to the execution of Mata Hari, a famous dancer and secret agent who worked as a spy for both the French and the Germans.
The famous writer Edgar Allan Poe, in 1840, loved to hack the ciphers of the time and even published an ad, in the Alexander’s Weekly Messenger of Philadelphia, in which he boasted of these skills. Just think, he thought he was so good that he asked to receive more cipher texts to decode!
We must give him credit, however, because his publication on cryptographic methods was very useful for British cryptographers who were thus able to crack German codes during World War I.
To admire the first cipher teletype with a preset key, we have to move to 1917 and have Gilbert Vernam to thank. Its operation was very simple, the key chosen had to be set on a punched tape and combined character by character so as to produce a cipher text. This system was called a one-time. It will sound beautiful too bad that the keys were as long as the text to be decoded!
Barely a year after the cipher teletype here appears on the scene the most famous decoding machine in history: the Enigma, invented by Arthur Scherbius. The Germans used it extensively during the war but a Polish officer, Rejewsky, is credited with its downfall. In fact, in 1932 he managed to figure out the internal details of the structure and revealed them to the intelligence of France and Britain.
An interesting peculiarity of the British spy department was that it was composed of numerous expert chess players and mathematics professors, including Alan Turing who is considered the founder of modern computer science.
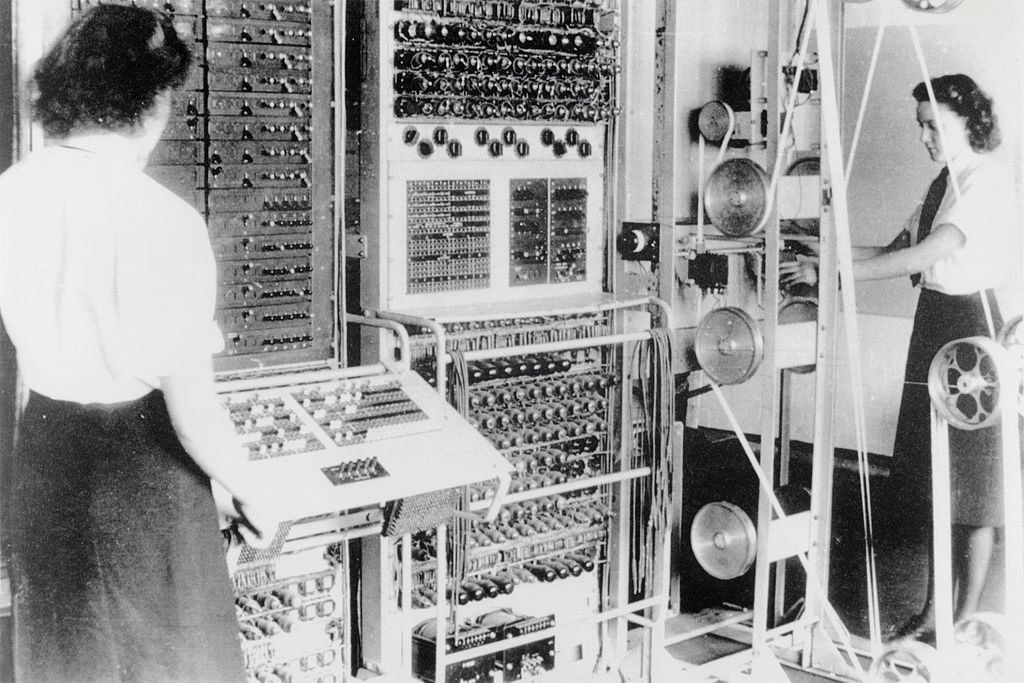
Thus, it was the British who invented the first programmable digital computer: The Colossus. This machine served them as an aid in deciphering encrypted messages from enemies. Imagine what hard work they did before!
Two machines used by the Allies very similar to Enigma that were never hacked, during World War II, are TypeX and SIGABA.
Instead, do you want to know a fun fact about British SEO and American special forces? Well, the former used poem ciphers to communicate, while the latter used codes based on Native American dialects. These native soldiers who were used for this task were called code talkers and used the dialect navajo.
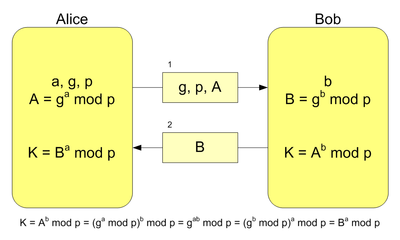
We have to get to 1976 with the publication of the New Directions in Cryptography to use a new method of distributing cryptographic keys. This was in fact one of the fundamental problems in this subject. This new exchange method is known as Diffie-Hellman, the names of the two inventors.
This new paper immediately led to the development of new encryption systems of asymmetric key algorithms. But here a whole other world opens up about the new cryptography…
As you have seen from our article, the story is also full of secret messages to be deciphered just like the puzzles to be solved escape room!
Now you just have to decipher the puzzles to solve an escape room with MysterU.
That’s it from Agent Camilla, now to the next historical article!